Creating GoldenGate Distribution Path in MarketPlace VM
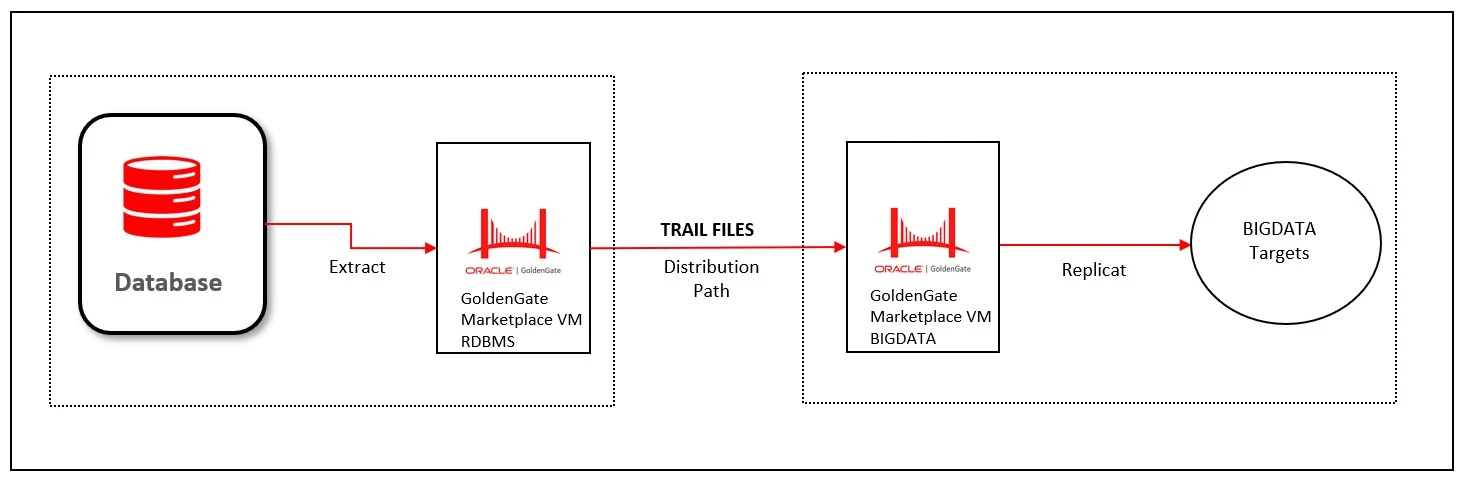
GoldenGate Distribution Path MarketPlace VM article describes all the steps in detail on how to create WSS secured Path between two Marketplace VM.. In this kind of scenario, there will be a situation where the trail files needs to be transported using a Distribution Path from Source VM to Target VM. Creating a Distribution Path and running it automatically creates a Receiver Path in the target deployment’s Receiver service. Data transactions are received by the Receiver Path from the source deployment’s Distribution service.
Pre-requisites
Here, I have provisioned 2 Marketplace Images.
Pre-requisites
- Provision 2 GG Marketplace VM’s
- Create a connection to a source database.
- Create an Extract for generating local trail file
Here, I have provisioned 2 Marketplace Images.
- GG Market place VM for Oracle database – Source
- GG Market place VM for BigData – Target
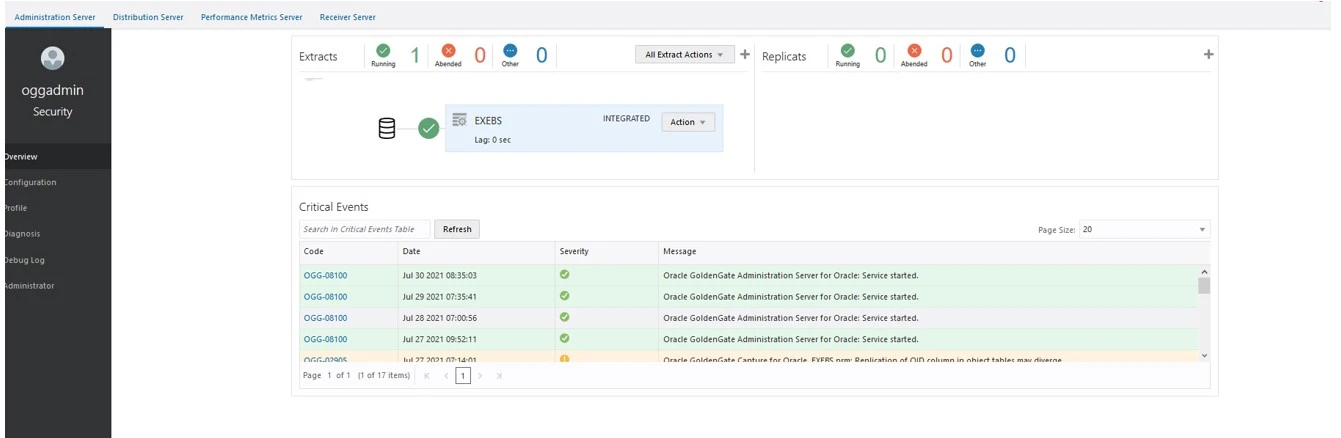
As per the pre-requisites, Extract has already configured for source EBS Instance and it is in RUNNING status.
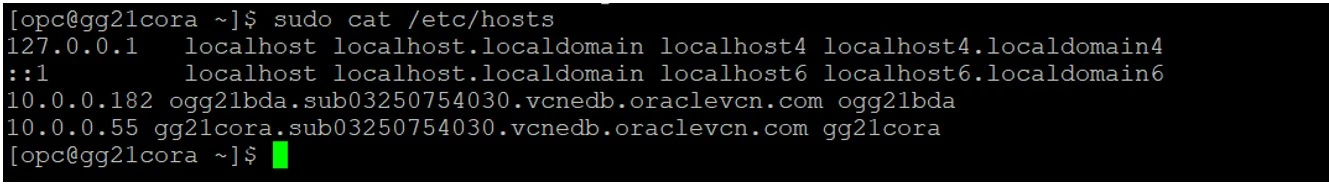
Add the target hostname & IP into source /etc/hosts
Download the certificates from Target VM
Use the browser to download the target certificate to trust the connection from source. The browser used here in this demo is Mozilla Firefox.
The target VM is GG21c for BigData.
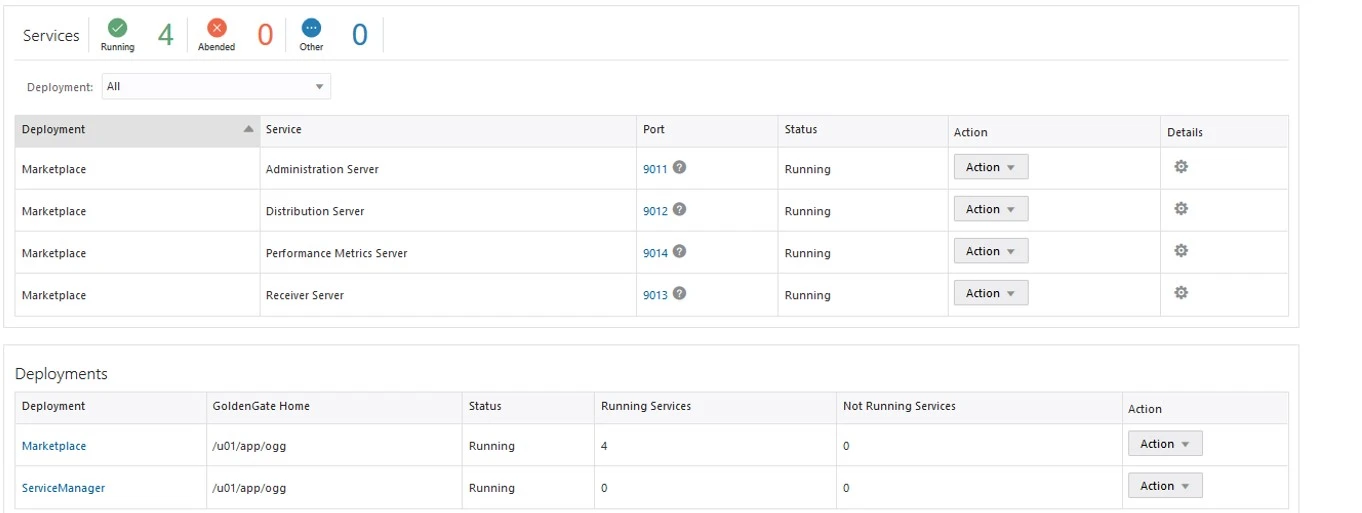
Login into the Target Service Manager Console using oggadmin credentials.
Deployment Name: Marketplace
On top left of the browser there is a lock icon. Click on that.
Click on Connection not Secure – More Information
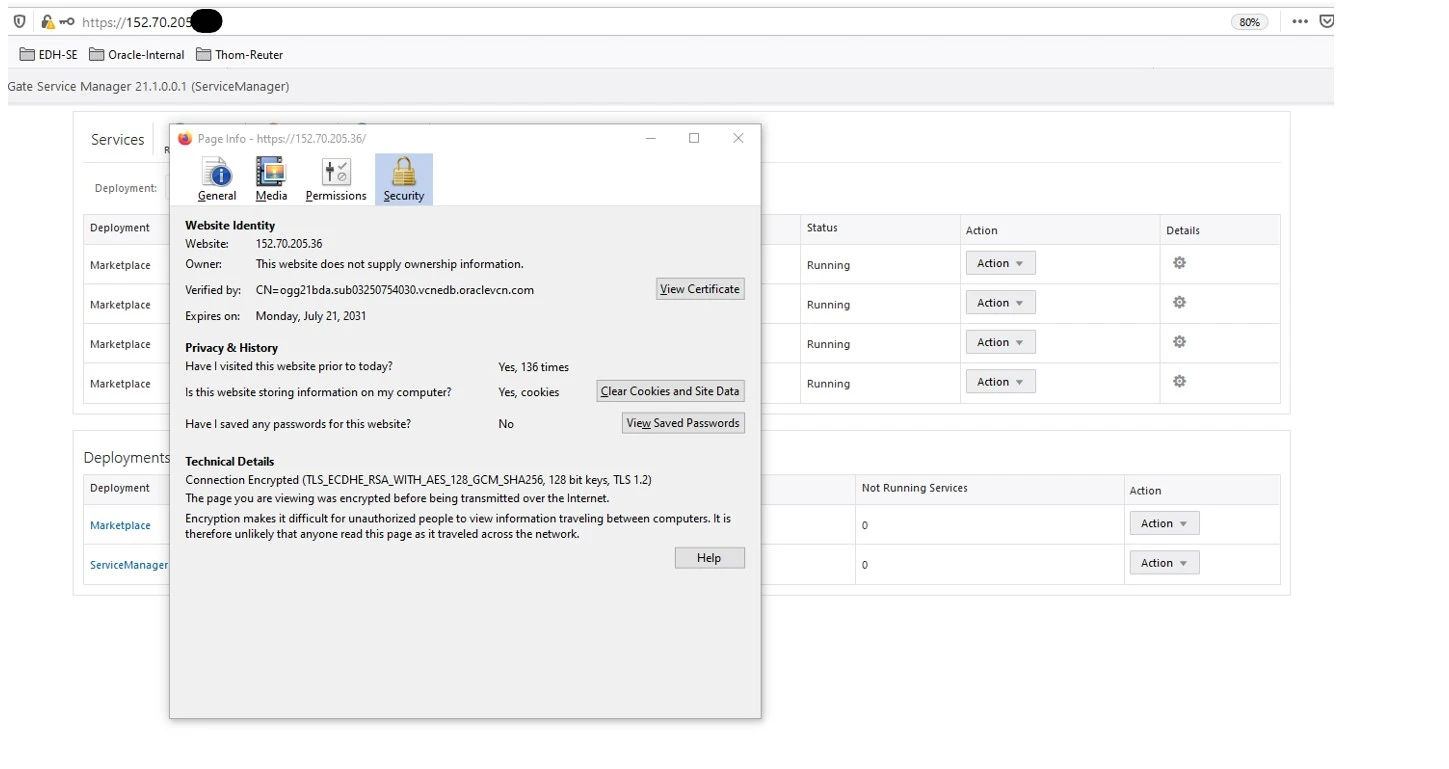
Click on view certificate and download PEM(Cert) PEM (chain) to the local directory!
Copy the private key from Target GG VM.
Login to the target GG VM, here in thist case it is GG BDA Marketplace VM.
Go to the directory /etc/nginx and cat the ogg.pem file.
Here is a sample output
Login to the target GG VM, here in thist case it is GG BDA Marketplace VM.
Go to the directory /etc/nginx and cat the ogg.pem file.
Here is a sample output
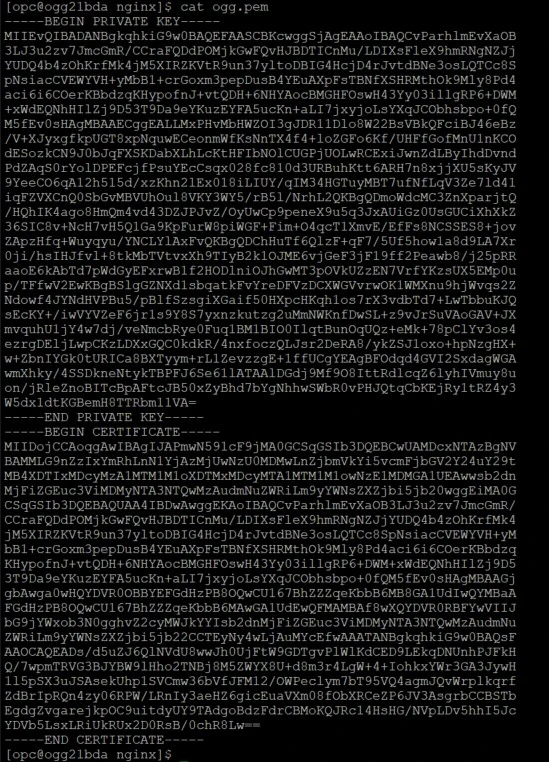
Here you see certificate information + the private key.
Copy only the private key from this file and store it locally in some text file.
Copy only the private key from this file and store it locally in some text file.
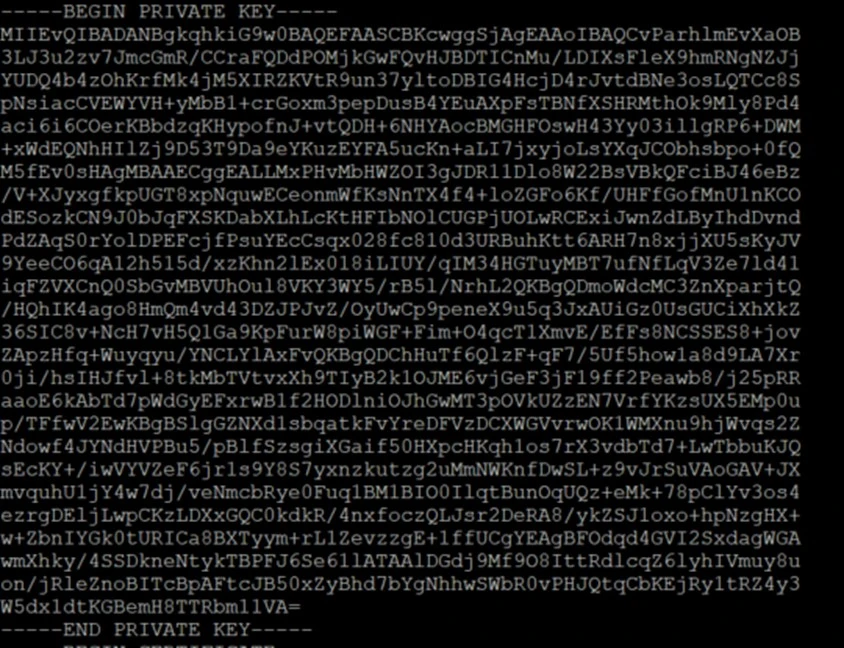
Import the certificates
Login to GG Source console Service Manager.
Select the appropriate deployment. In this case I am using Marketplace deployment.
Login to GG Source console Service Manager.
Select the appropriate deployment. In this case I am using Marketplace deployment.
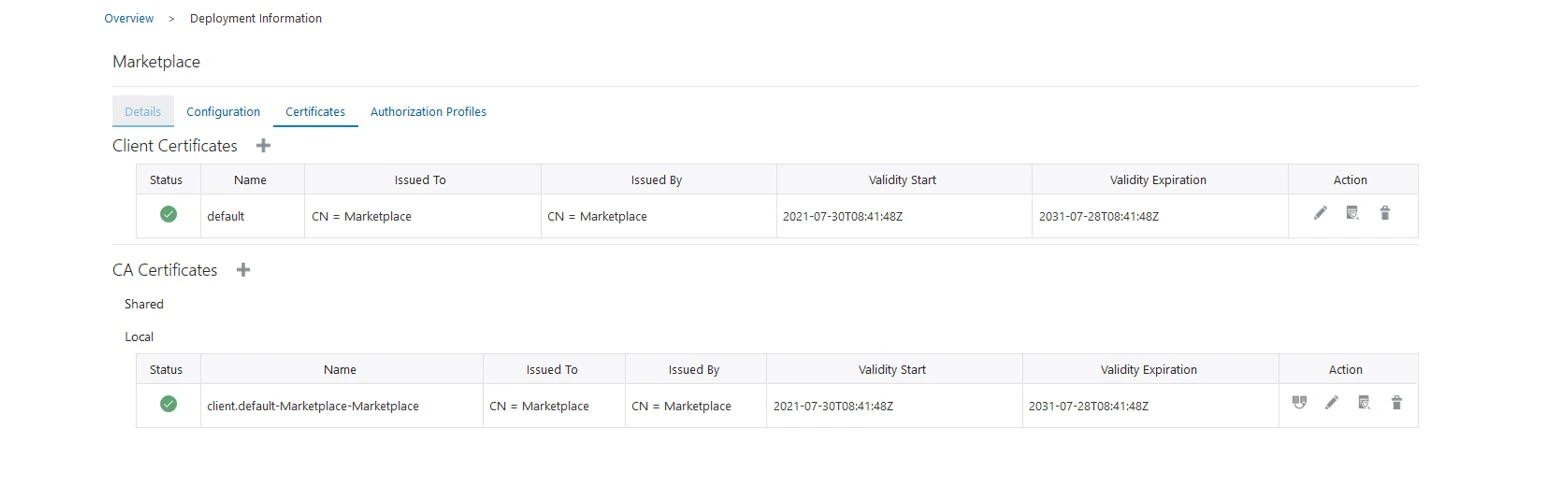
Click on the Marketplace Deployment and select the certificates tab. Initial certificate tab looks like below screenshot with one client certificate and one CA Certificate.
Import the CA Certificates.
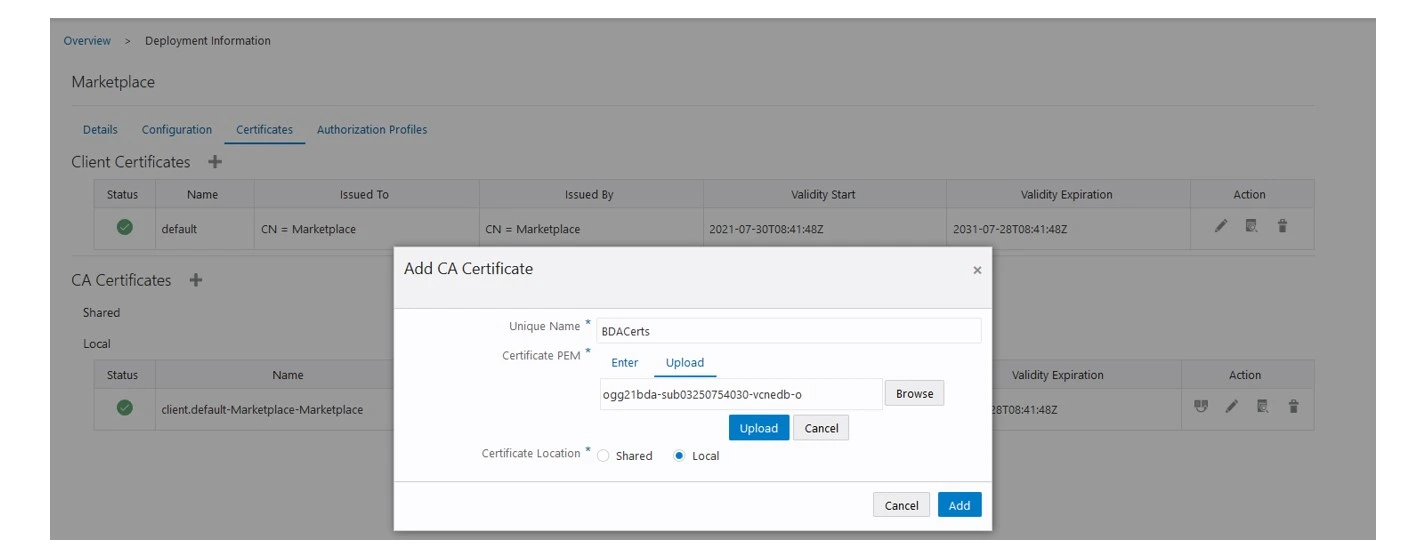
Add CA Certificates, click on +
Add CA Certificates, click on +
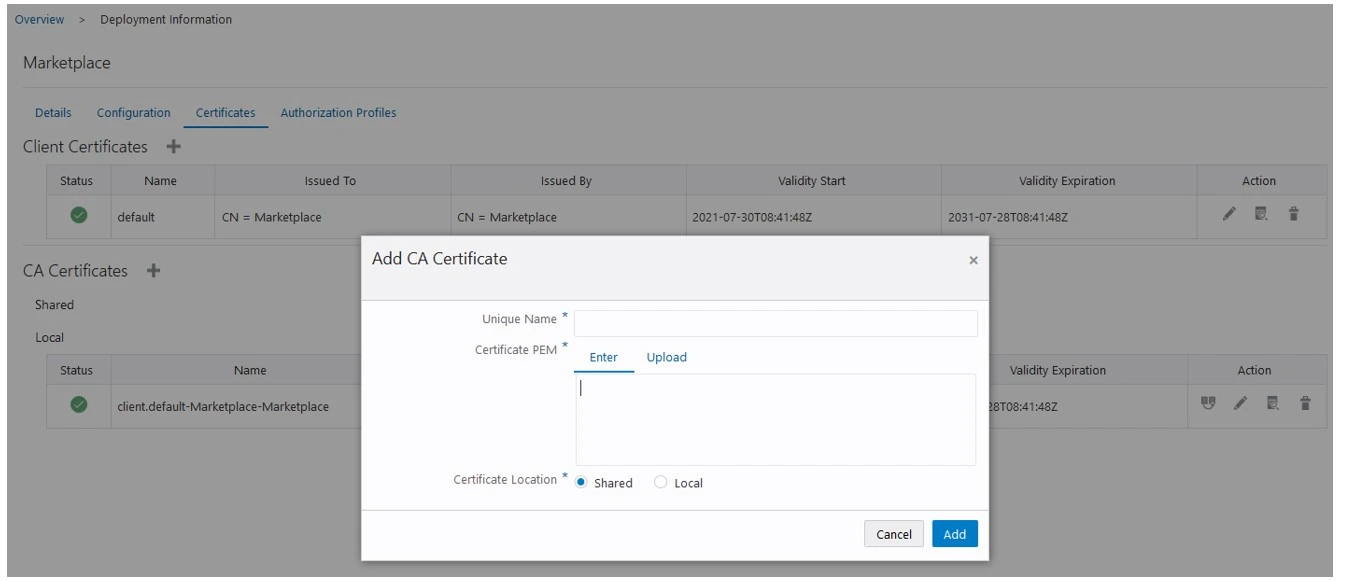
Select local certificate tab and provide a unique name.
Here in the below Example I have given BDAcerts as a unique name.
Select the downloaded chain.pem file & click on upload
Here in the below Example I have given BDAcerts as a unique name.
Select the downloaded chain.pem file & click on upload
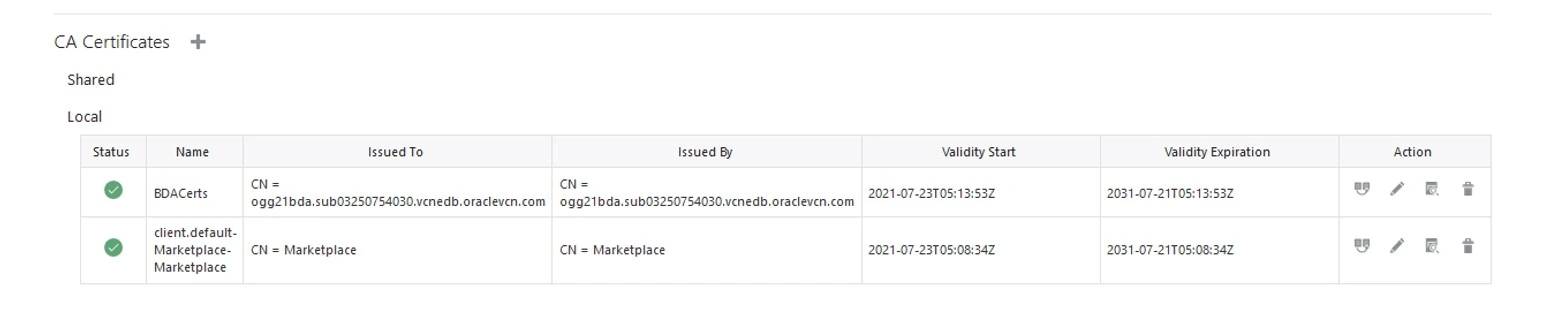
After the upload, you will see 2 CA Certificates.
One is the local and the other one is the target one.
One is the local and the other one is the target one.
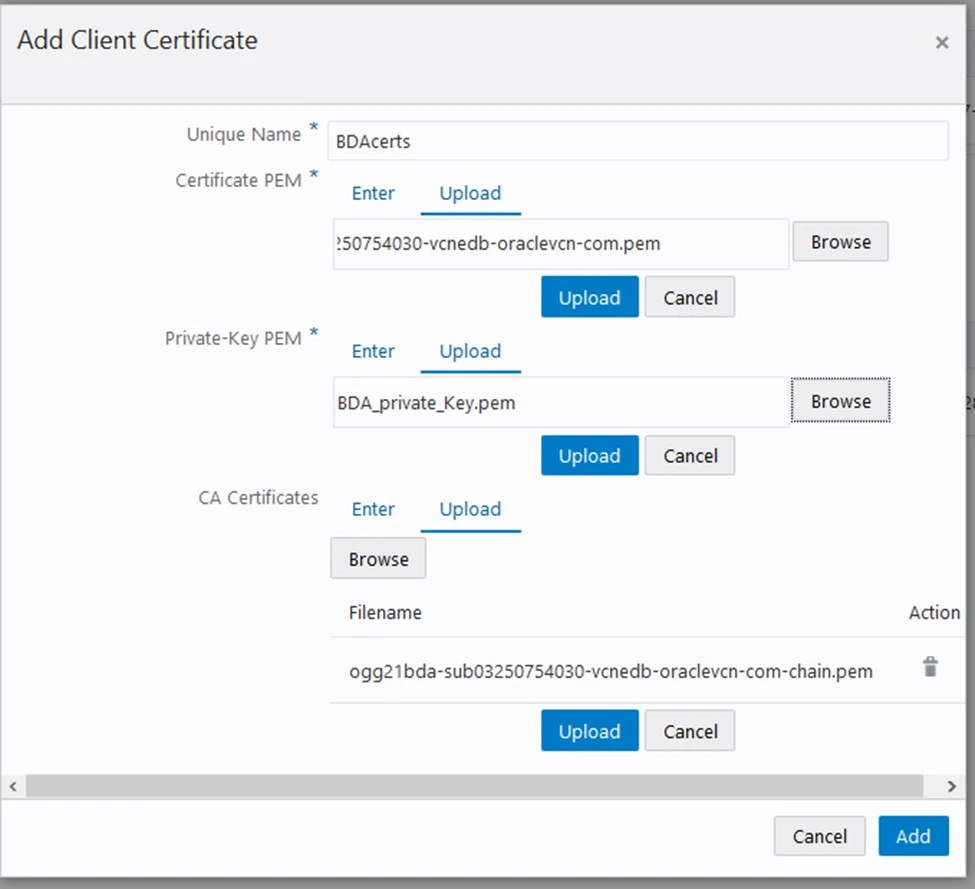
Import the Client Certificates.
Click on Client Certificates +
Provide a Unique Name : BDAcerts as an example.
Certificate PEM : Target PEM
Private key : Target Private key from ogg.pem
CA Certificates : Target chain.pem
Click on Client Certificates +
Provide a Unique Name : BDAcerts as an example.
Certificate PEM : Target PEM
Private key : Target Private key from ogg.pem
CA Certificates : Target chain.pem
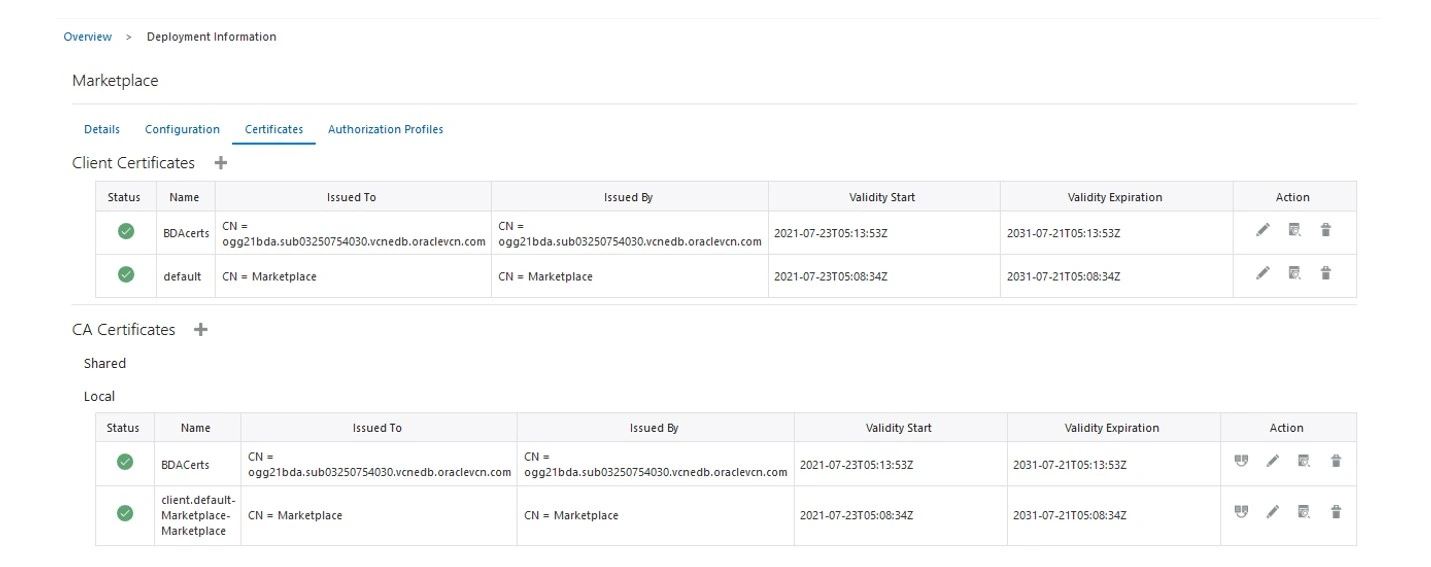
Final Screen shot after adding the certificates
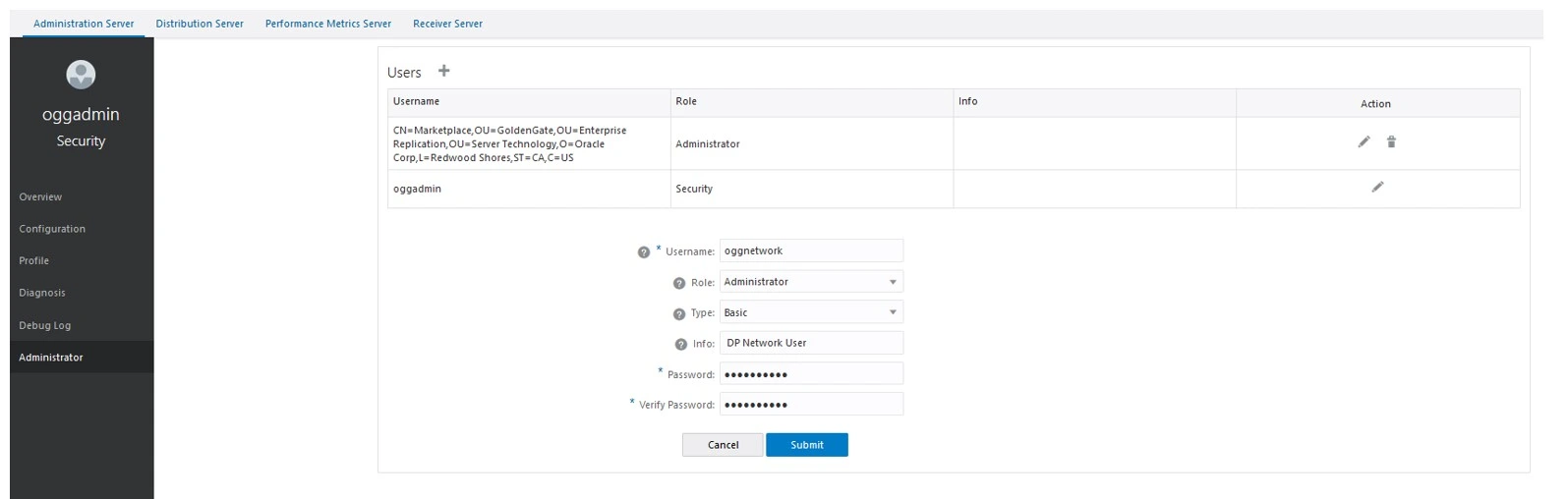
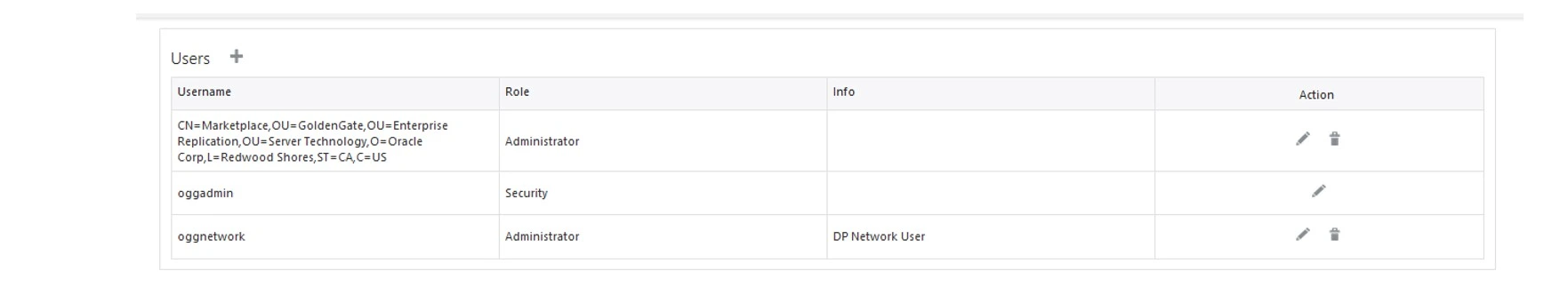
Add User in Target VM.
Login to Target Administration Server – Click on Hamburger -> click on Administrator.
Click on Users +
Login to Target Administration Server – Click on Hamburger -> click on Administrator.
Click on Users +
Add Configuration on Source VM.
Make sure you provide the same username & password that was given in target server. In this case it is oggnetwork/password
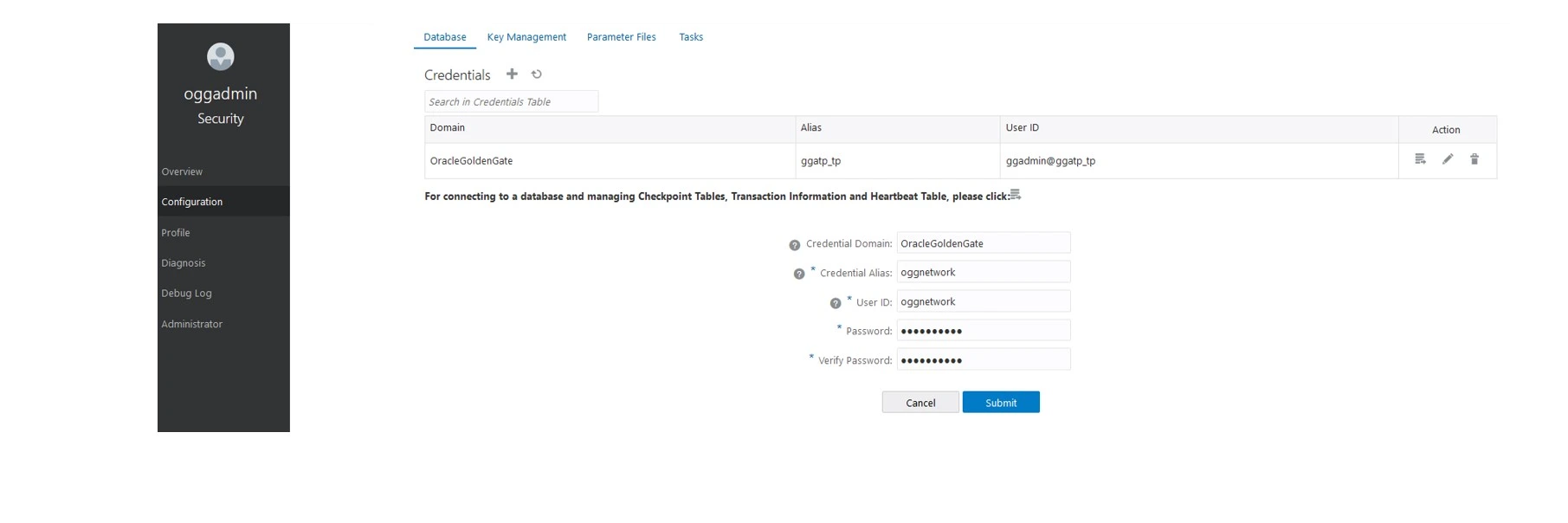
- Login to Source Administration Server – Click on Hamburger -> click on Configuration+
- Click on Credentials +
Make sure you provide the same username & password that was given in target server. In this case it is oggnetwork/password
Add Distribution Path
- Click on + to add a Path.
- Make sure to add Correct target Deployment Name, Domain Name, Alias as created in the previous steps.
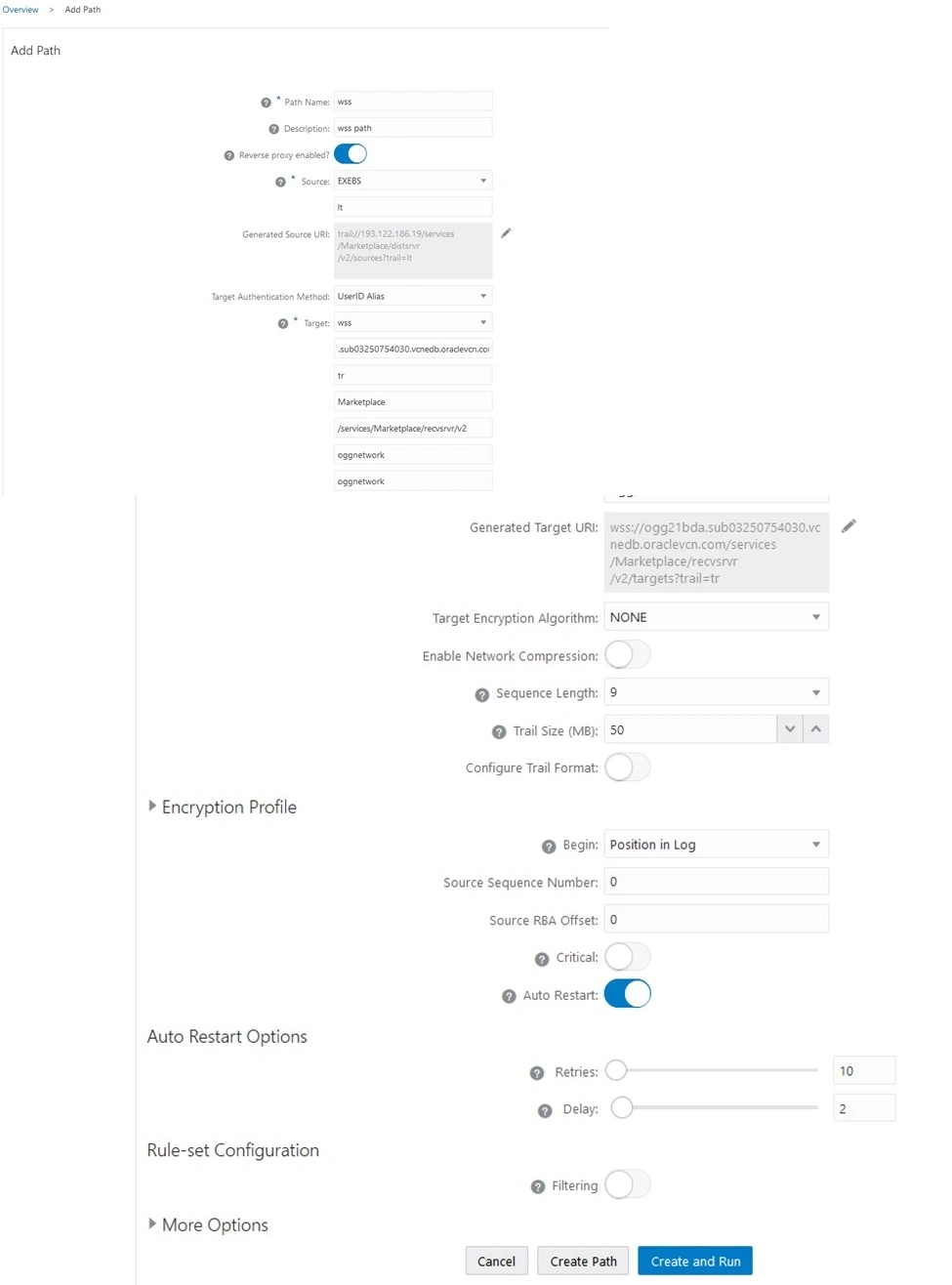
Final screenshot of the PATH created using WSS.
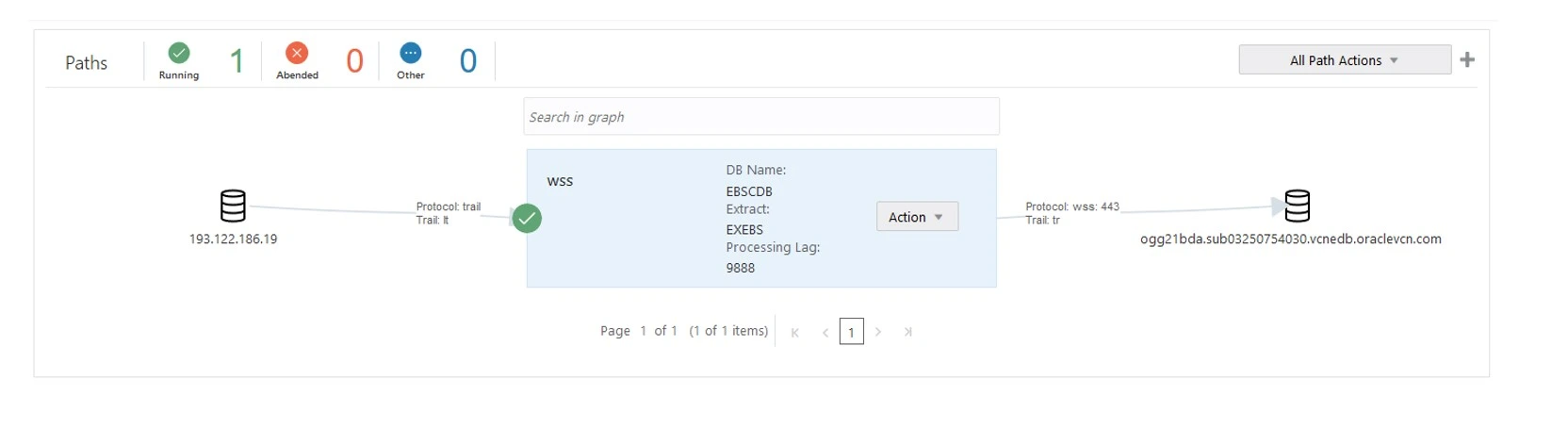
NOTE : In some cases Reverse proxy enabled is not required to be on and do not modifiy Generated Target URI path with the custom directory.
For more information on Distribution Path can be found at Oracle documentation here.
That’s it. Now the Distribution Path across 2 different VMs are established and the trail files will be placed on to the target VM….. Hope you found this article useful.Disclaimer: The views expressed on this document are my own and do not necessarily reflect the views of Oracle..
That’s it. Now the Distribution Path across 2 different VMs are established and the trail files will be placed on to the target VM….. Hope you found this article useful.Disclaimer: The views expressed on this document are my own and do not necessarily reflect the views of Oracle..
